Microsoft products have historically been cited as the system that hackers love to attack. However, as hackers have become wilier and more determined, and the pressure for rapid system updates has led more companies to take shortcuts with their release cycles, no OS—desktop or mobile—is safe, anymore.
Recently, a spate of bad news has hounded Apple, with flaws being revealed and scams proliferating. Following are a few issues Carmichael’s Apple users should be aware of at the present time.
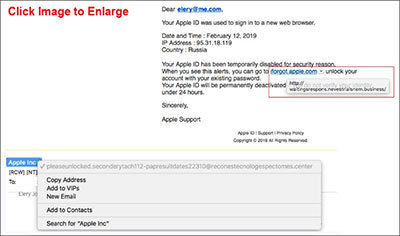
Apple “Account Disabled” Phishing Attack:
Hackers are targeting Apple users with a new phishing scam. This one reports that questionable activity has occurred in the user’s account, resulting in their Apple ID being disabled for security reasons.
The email further asks the user to go through an Apple ID verification process that is initiated by clicking one or more links. This is an attempt to harvest personally identifiable information (PII).
Apple users who receive this email should take no action other than reporting it to Apple’s legal team.
Users who want reassurance their Apple ID has not been compromised can sign into the account from apple.com and confirm it is still active. However, this is not necessary.
 Dangerous at Every Level
Dangerous at Every Level
If someone starts the process of responding to the email, they will be led through a series of questions about their PII, clicking a button that says “Next” after each confirmation. Clicking this button will immediately send that particular response to the hackers, so backing out of the process after starting it will not eliminate the threat of exposure.
The best way to avoid being compromised is to ignore (and preferably delete) the email. However, users can safely hover over the links with their mouse, which will show them the web address of the malicious site.
Apple “Snooping Bug”: An 18-year-old computer whiz recently discovered a vulnerability affecting the latest Apple macOS that leaves stored passwords open to malicious apps. That could include logins for bank websites, online services like Amazon, cloud-based apps and platforms like Slack, and many more. And, while this bug is technically limited to Macs, the flaw is inside the Apple “keychain.” That’s where the macOS stores private keys and passwords. Anyone who has an iCloud keychain is likely having their passwords synched across all devices, so iPhone passwords will be vulnerable, too.
The kicker? The hacker’s mock malware didn’t need administrator-level privileges or any other special permissions to access the private information. The flaw was wide open. This news comes on the heels of another teenager discovering an Apple vulnerability, this one in FaceTime. Apple paid for the details on this flaw and likely has it closed by now, but at the time of this writing, the “keychain” flaw was not closed.
The most robust defense against the keychain vulnerability is to manually set a password for it. That will mean that every time a legitimate application wants to use a password from the keychain, the user will have to enter the login. It’s a hassle, but it’s the safest bet.
The lesson in these new threats is two-fold.
- Apple products and operating systems continue to be prime targets for cybercriminals, as are all extremely popular systems.
- n the current, threat-laden environment, sometimes security wins over usability.
At Carmichael, we don’t expect the situation to change, anytime soon. To request future updates from Carmichael Consulting, email [email protected]. To request a vulnerability assessment of your Apple hardware, give us a call at 678-719-9671.

